Quality Modeller Cloud Security Information
If using Quality Modeller through Curiosity’s cloud, i.e as a SaaS product, the software is hosted on Amazon Web Services (AWS).
In this instance, security and compliance is a shared responsibility between AWS and Curiosity:
AWS responsibility “Security of the Cloud” - AWS is responsible for protecting the infrastructure that runs all the services offered in the AWS Cloud. This infrastructure is composed of the hardware, software, networking, and facilities that run AWS Cloud services. The AWS Cloud services that Curiosity use are as follows; ECS, RDS, EC2, Route53, and SecretsManager.
Curiosity responsibility “Security in the Cloud” – Curiosity responsibility is determined by the AWS Cloud services selected, as mentioned previously these are ECS, RDS, EC2, Route53, and SecretsManager. More information about the security configurations applied to each AWS Cloud service are detailed below.
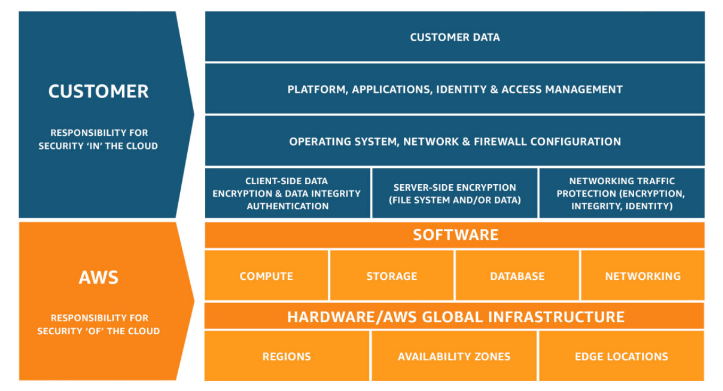
All AWS Cloud services used by Curiosity are managed services, therefore, as illustrated above, they are all protected by the standard AWS global network security procedures. These are discussed in length in the Amazon Web Services: Overview of Security Processes whitepaper.
Security in Amazon Elastic Container Service (ECS) and EC2
Amazon ECS and EC2 are container management services used to run, stop, and manage containers on a cluster. Third-party auditors assess the security and compliance of these services as part of multiple AWS compliance programs including SOC, PCI, FedRAMP, HIPAA, and others.
Access to Amazon ECS and EC2 is managed by AWS Identity and Access Management (IAM) to protect and manage AWS accounts in a way that each user is given only the permissions necessary to fulfil their job duties. Monitoring is a crucial part of maintaining containers, therefore, Curiosity uses CloudWatch logs, alarms, and events to monitor and manage the status of the containers.
Curiosity also use transport layer security (TLS) for the HTTPS connection into the EC2 LoadBalancer to ensure maximum security between the two endpoints. This Elastic Load Balancer uses a Secure Socket Layer (SSL) negotiation configuration to negotiate SSL connections between a client and the load balancer. The security policy used here is the default 'ELBSecurityPolicy-2016-08' which ensures that all data passed between the endpoints is private.
AWS Elastic Compute Cloud (EC2) runs complementary to ECS and therefore the same security information applies.
Security in Amazon Relational Database (RDS)
Amazon RDS is a collection of managed services that makes it simple to set up, operate, and scale databases in the cloud.
Access to Amazon RDS is managed by AWS Identity and Access Management (IAM) to protect and manage AWS accounts in a way that each user is given only the permissions necessary to fulfil their job duties.
Curiosity use PostgresSQL, run in a virtual private cloud (VPC) based on the Amazon VPC service, to ensure network-level isolation. TLS and SSL is not required for the connection between the Curiosity products' APIs and the PostgresSQL database because both are hosted in the same VPC.
Security in Amazon Route 53
Amazon Route 53 is a cloud domain name system (DNS) service that enables the customisation of DNS routing policies to reduce latency, improve application availability, and maintain compliance.
Access to Amazon route 53 is managed by AWS Identity and Access Management (IAM) to protect and manage AWS accounts in a way that each user is given only the permissions necessary to fulfil their job duties.
Steps are taken to ensure Curiosity never puts confidential or sensitive information into tags or free-form fields such as the name field as any data entered in these fields can be used for billing or diagnostic logs.
Security in Amazon Secrets Manager
AWS Secrets Manager helps protect, rotate, manage, and retrieve database credentials, API keys, and other secrets throughout their lifecycle. This is a built in integration for Amazon Relational Database Service (Amazon RDS).
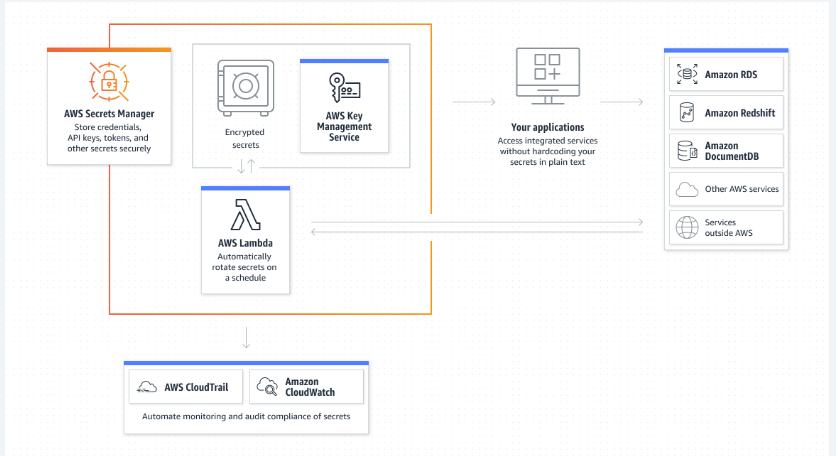
Access to Amazon Secrets Manager is managed by AWS Identity and Access Management (IAM) to protect and manage AWS accounts in a way that each user is given only the permissions necessary to fulfil their job duties. When using the AWS CLI to invoke AWS operations unrelated to Security Manager, any risks are mitigated by taking steps including:
- Always lock your computer when you walk away from your console
- Uninstall or disable console utilities you don't need or no longer use.
- Ensure the shell or the remote access program, if you are using one or the other, don't log typed commands.
Secrets Manager uses built-in encryption with AWS Key Management Services (KMS) keys and data keys to protect each secret value. Whenever the secret value changes, Secrets Manager generates a new encrypted data key to protect it.
User Credential Management
Curiosity use Auth0, a cloud service that provides a set of unified APIs and tools that enables single sign-on and user management for Quality Modeller.
Auth0 is compliant with many standards including ISO27001, SOC 2 Type 2, ISO27018, HIPAA BAA, Gold CSA STAR, PCI DSS, and GDPR.
Quality Modeller also supports SSO via ADFS, OIDC, Azure AD, LDAP and more.


